The reliable infrastructure for anti-DDOS protection services
Remote Triggered Firewall is a DTEL-IX initiative to create a stable infrastructure to develop and maintain reliable networks protected from DDOS-atacks.
Як відбувається обмін трафіком у звичайних умовах
Under normal circumstances, IXP Customer receives traffic from all other customers and this traffic fits the the bandwidth of customer’s connection to IXP network.
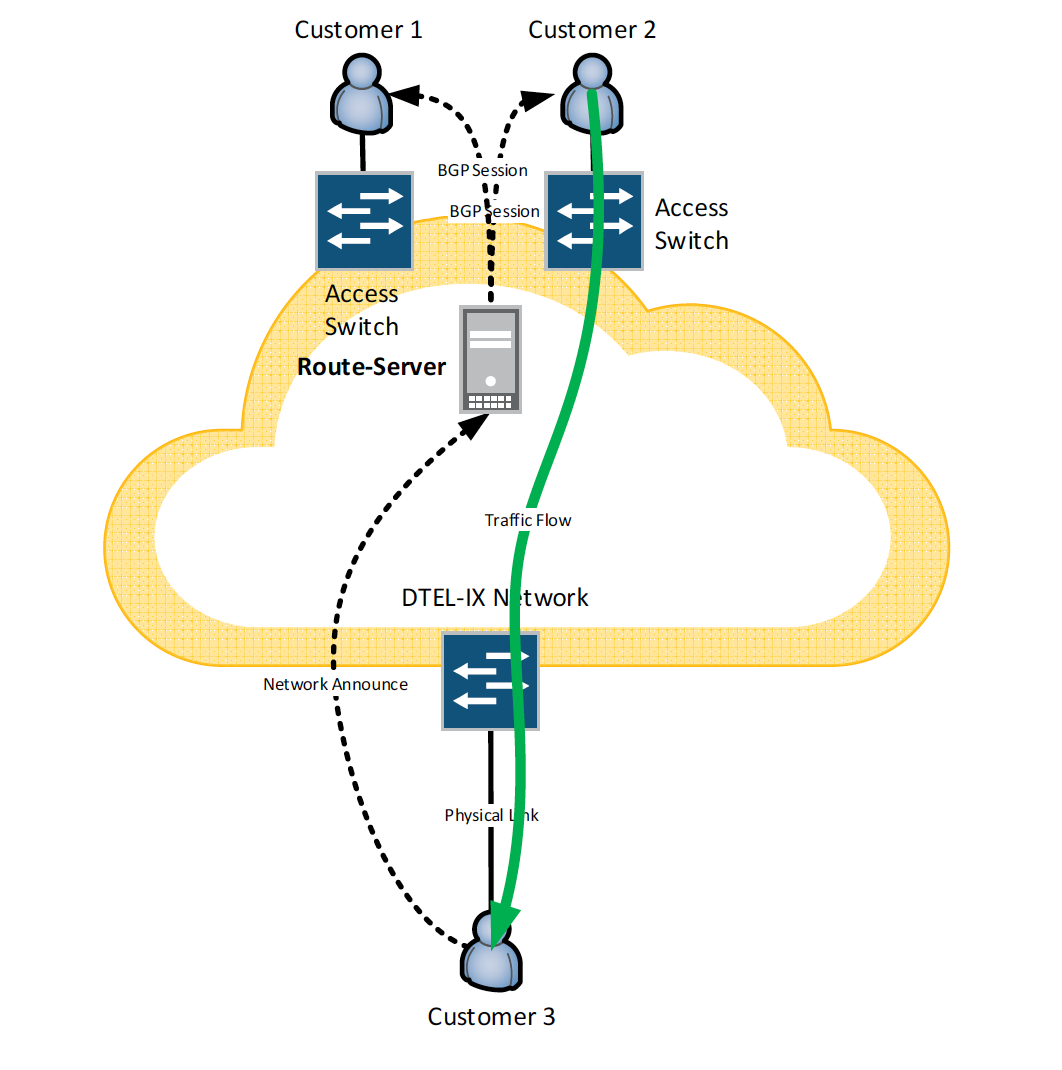
In such case Victim Customer might want to filter out malicious traffic in order to get it off from its connection to DTEL-IX network.
Учасник потрапив під DDOS-атаку
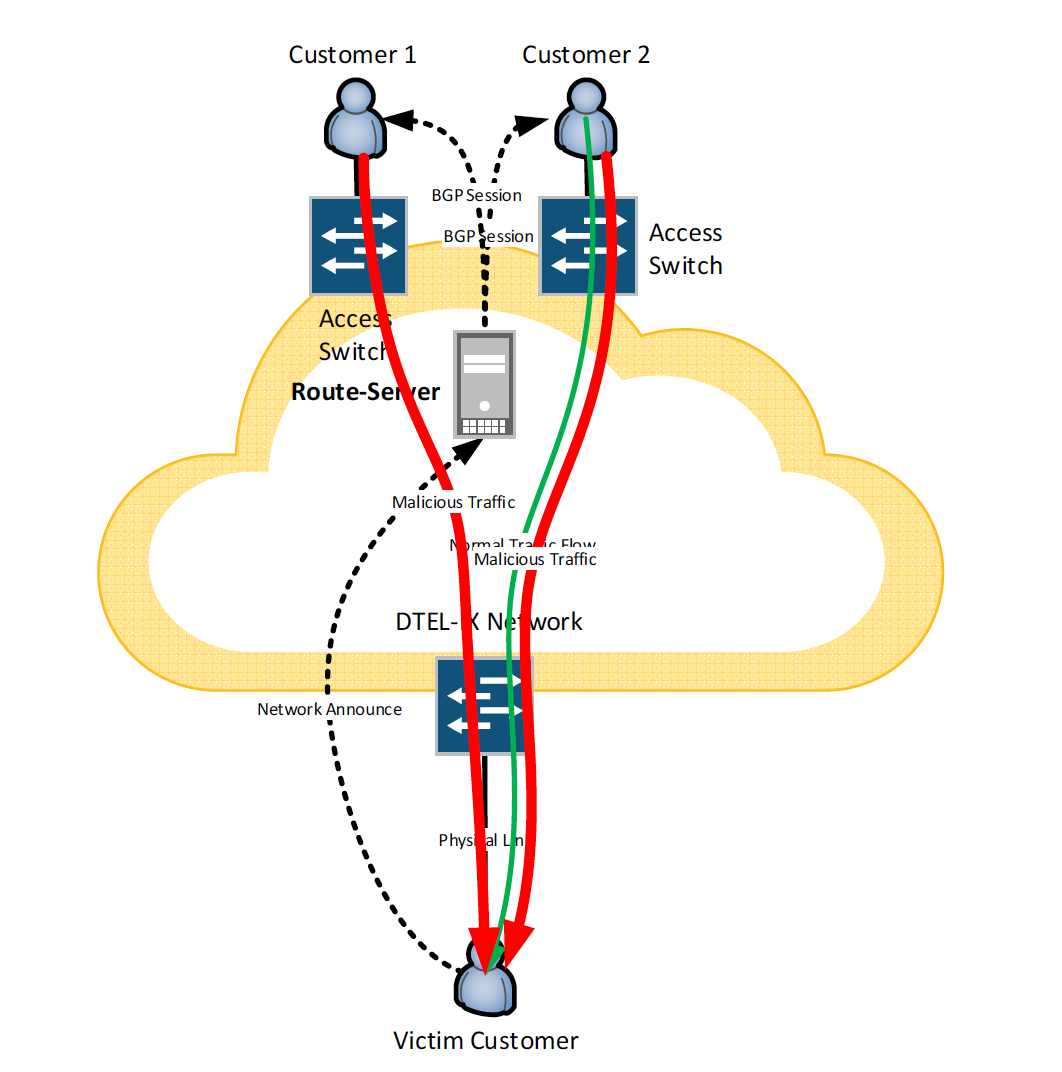
Under DDOS attack the Victim Customer starts to receive much more malicious traffic from other customers and this flood causes overloading of its connection, leading to massive packet loss and service degradation.
Анонси префіксів на Route Server з підтримкою flowspec
DTEL-IX Remote Triggered Firewall (RTFW) allows customers to redirect traffic flow to any of their networks to special firewall and instruct it what traffic should be dropped. How does it work? DTEL-IX implemented special separate Route Server which supports BGP FlowSpec, and a dedicated firewall which is able to receive BGP FlowSpec routes from RTFW Route Server
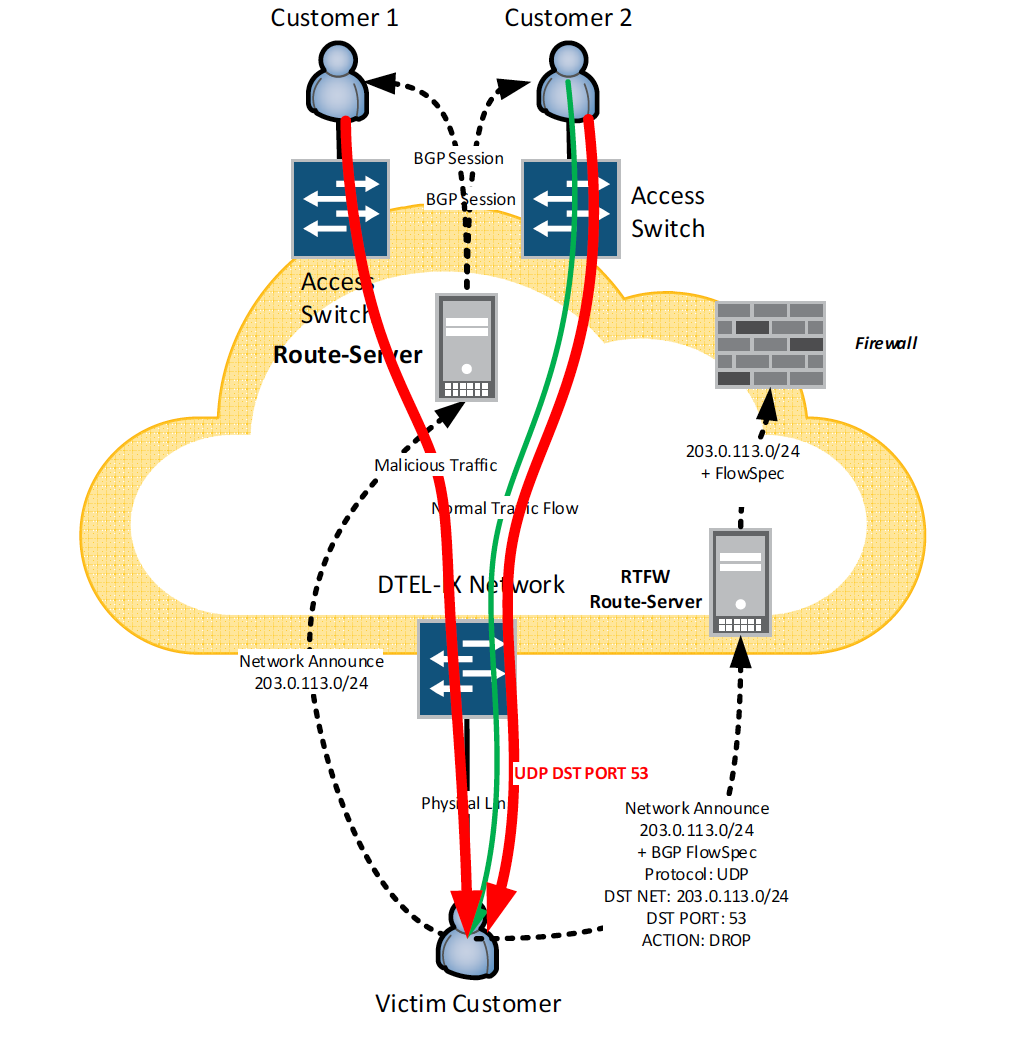
Задіянн спеціального файрвола на базі Juniper MX 10003
In its turn firewall announces corresponding networks to unicast IPv4/IPv6 servers, causing all other customers to send traffic to Victim Customer via itself. Malicious traffic will be dropped, and clear traffic will be delivered to Victim Customer:
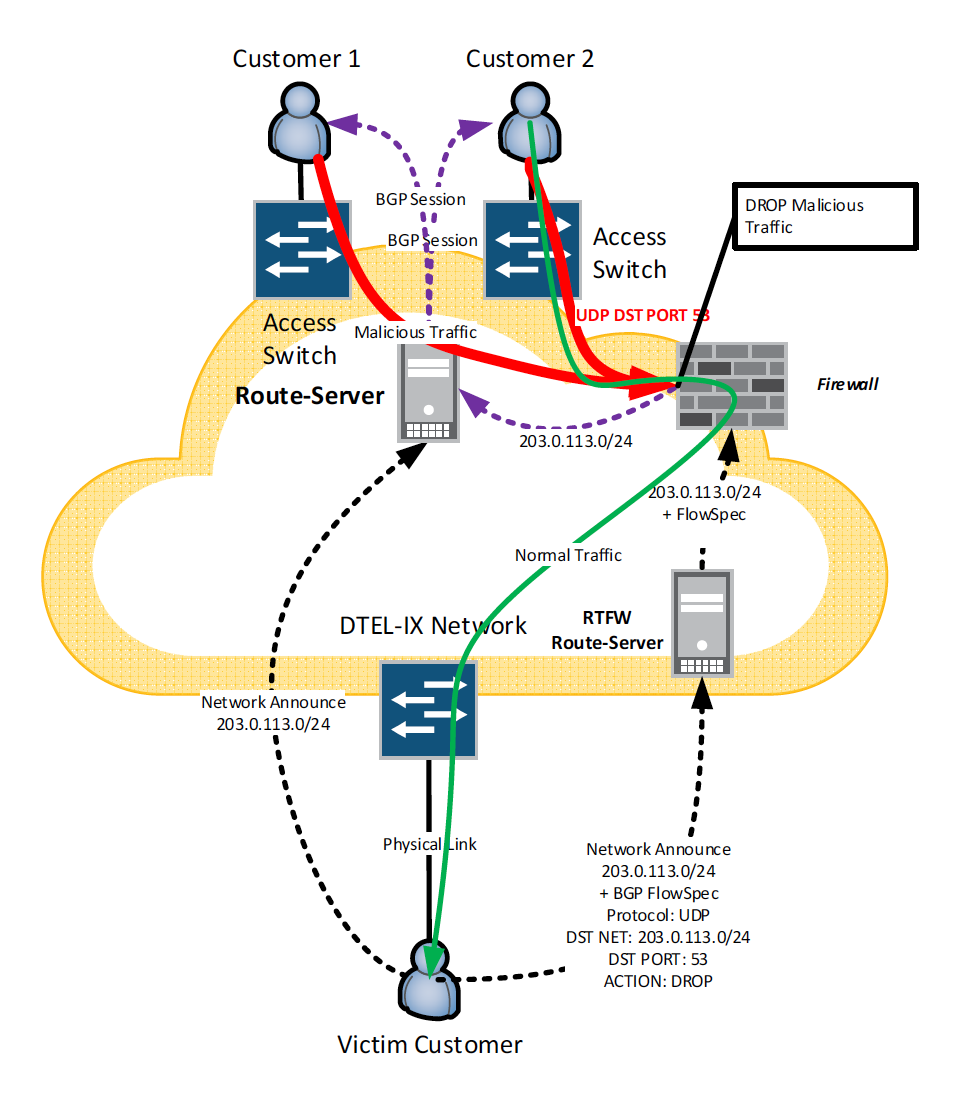
Moreover, any customer which router supports BGP FlowSpec, can establish BGP connection to RTFW Route Server and receive BGP FlowSpec routes directly. This lets to drop malicious traffic on customers’ networks, so it will not enter DTEL-IX network.
